From Wikipedia, the free encyclopedia
More Details about the Fake Anti-spyware Programs: A fake anti-spyware program is a malicious program that can infect various versions of Windows operating system such as Windows 7, Windows 8, Windows xp and so on. So, basically I have had Anti-Spyware on my personal PC, since sometime in 2000. Over the years, I have changed anti-spyware programs, but mainly stay within the original programs that are tried and proven, Ad-Aware, CCleaner, SpyBot Search & Destroy, Malwarebytes, AVG, Avast!, and a couple of others. I have also, discovered Glarysoft software. System Check is a fake anti-spyware designed to convince the users that their systems are infected and to make them reveal their sensitive credit card information. The rogue belongs to FakeHDD family and is almost the exact copy of System Fix.
The 11 Best Free Spyware Removal Tools Here are the best anti-spyware software programs out there today. System Check is a fake anti-spyware designed to convince the users that their systems are infected and to make them reveal their sensitive credit card information. The rogue belongs to FakeHDD family and is almost the exact copy of System Fix. It enters your compute exploiting the vulnerable sides of your system and begins its nasty work.
Rogue security software is a form of computer malware that deceives or misleads users into paying for the fake or simulated removal of malware. Rogue security software, in recent years, has become a growing and serious security threat in desktop computing.[1]
Propagation
Rogue security software mainly relies on social engineering in order to defeat the security built into modern operating system and browser software and install itself onto victims' computers.[1]
The book succeeds in being reasonably self-contained. The sliding mode control methodology has proven effective in dealing with complex dynamical systems affected by disturbances, uncertainties and unmodeled dynamics. From the book reviews: “This book covers several different topics related to sliding mode control and observation. Sliding Mode Control and Observation represents the first textbook that starts with classical sliding mode control techniques and progresses toward newly developed higher-order sliding mode control and observation algorithms and their applications. Sliding mode control theory. Robust control technology based on this methodology has been applied to many real-world problems, especially in the areas of aerospace control, electric power systems, electromechanical systems, and robotics.
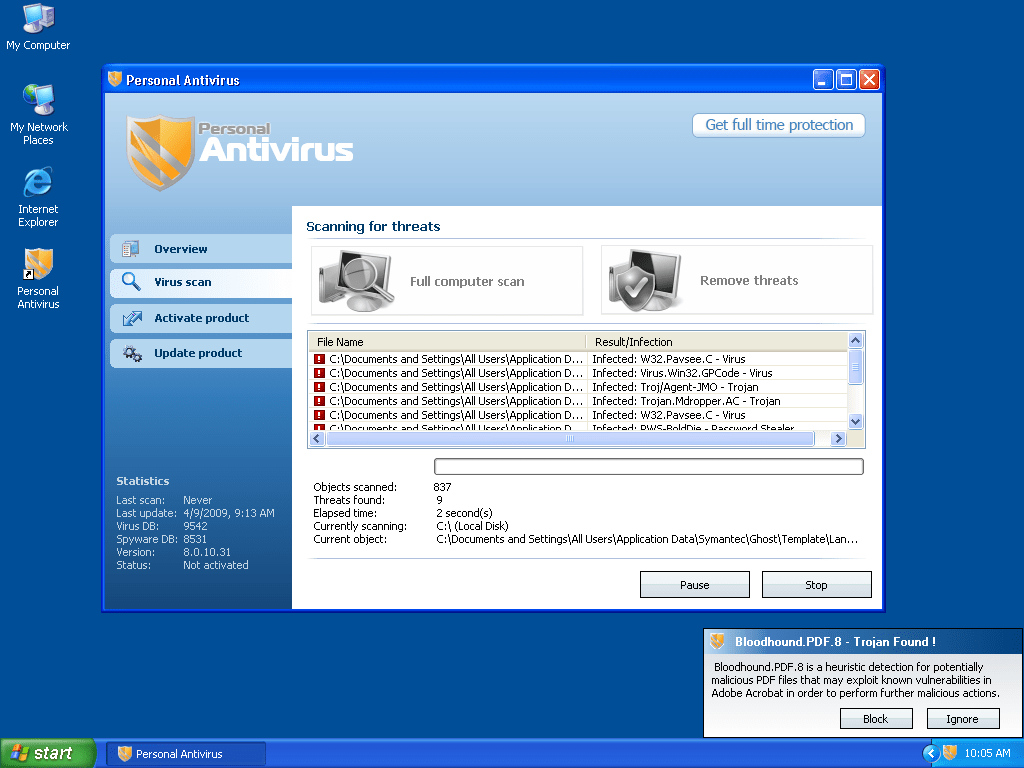
Most have a Trojan horse component, which users are misled into installing. The Trojan may be disguised as:
Titanic title song. Beautiful Koyal Real Sound Mp3 - Good Morning (00:06) Dil Mil Gaye Mp3 Ringtone - Instrumental Music Serial Tone Star One (00:17) English Movie Titanic Instrumental Mp3 Ringtone - In Pan Pipe Roamantic My Heart Will Go On (00:26) Excellent Dhol Music Instrument With English Song - Rapture Dhol Ringtone (00:29) Nokia Tune Dhol Mix Mp3 Ringtone (00:15) Violin Music Instrumental Mp3 Ring Tone - Sweet Violin Music (00:28). Random Mixed english movie and hindi movie instruments, Dhol and violin mix instrumental ringtones and real indian koyal mp3 instrumental Ringtones.
- A browser plug-in or extension (typically toolbar)
- An image, screensaver or archive file attached to an e-mail message
- Multimedia codec required to play a certain video clip
- Software shared on peer-to-peer networks[2]
- A free online malware scanning service[3]
Some rogue security software, however, propagate onto users computers as drive-by downloads which exploit security vulnerabilities in web browsers, pdf viewers, or e-mail clients to install themselves without any manual interaction.[2][4]
More recently, malware distributors have been utilizing SEO poisoning techniques by pushing infected URLs to the top of search engine results about recent news events. People looking for articles on such events on a search engine may encounter results that, upon being clicked, are instead redirected through a series of sites[5] before arriving at a landing page that says that their machine is infected and pushes a download to a 'trial' of the rogue program.[6][7]
Operation
Once installed, the rogue security software may then attempt to entice the user into purchasing a service or additional software by:
- Alerting the user with the fake or simulated detection of malware or pornography.[8]
- Displaying an animation simulating a system crash and reboot.[1]
- Selectively disabling parts of the system to prevent the user from uninstalling them. Some may also prevent anti-malware programs from running, disable automatic system software updates and block access to websites of anti-malware vendors.
- Installing actual malware onto the computer, then alerting the user after 'detecting' them. This method is less common as the malware is likely to be detected by legitimate anti-malware programs.
Developers of rogue security software may also entice people into purchasing their product by claiming to give a portion of their sales to a charitable cause. The rogue Green antivirus, for example, claims to donate $2 to an environmental care program for each sale made. [9]
Some rogue security software overlaps in function with scareware by also:
- Presenting offers to fix urgent performance problems or perform essential housekeeping on the computer.[8]
- Scaring the user by presenting authentic-looking pop-up warnings and security alerts, which may mimic actual system notices.[10] These are intended to leverage the trust of the user in vendors of legitimate security software.[1]
Sanction by the FTC and the increasing effectiveness of anti-malware tools since 2006 have made it difficult for spyware and adware distribution networks—already complex to begin with[11]—to operate profitably.[12] Malware vendors have turned instead to the simpler, more profitable business model of rogue security software, which is targeted directly at users of desktop computers.[13]
Rogue security software is often distributed through highly-lucrative affiliate networks, in which affiliates supplied with Trojan kits for the software are paid a fee for every successful installation, and a commission from any resulting purchases. The affiliates then become responsible for setting up infection vectors and distribution infrastructure for the software.[14] An investigation by security researchers into the Antivirus XP 2008 rogue security software found just such an affiliate network, in which members were grossing commissions upwards of $USD150,000 from tens of thousands of successful installations per month.[15]
Restart the phone. Now you can any bangla text in your mobile phone. ** If you want to remove bangla font, delete the 'Fonts' folder or rename to another by computer. Bangla support write and read software download for nokia e72. Alternatively take out memory card before restart.
Unreal tournament 2004 v3369 private windows server patch. Unreal Tournament 2004 v3204 PRIVATE LINUX SERVER/CLIENT PATCH Unreal Tournament 2004 v1.0 Public Version +1 TRAINER Unreal Tournament 2004 MASTER SERVER BLOCKER. Unreal Tournament 2004 Patch v3369. This patch will updated your first person shooter Unreal Tournament 2004 to version 3369 fixing many different things including mod support and gameplay. ===== Unreal Tournament 2004 Patch 7 Release notes. ===== This patch is completely compatible with the retail version - servers and clients of any flavor. Jun 30, 2013 [UT2004] Unreal Tournament 2004 Patch v3369 June 30, 2013 Category: [UT2004] Patches, UT2004 Comments: 3 comments This patch will updated your first person shooter Unreal Tournament 2004 to version 3369 fixing many different things including mod support and gameplay.
Law enforcement
Top Anti Spyware Programs
In December 2006, the Washington Attorney General announced that it had reached settlement in a suit against Secure Computer LLC, the White Plains-based vendor of the Spyware Cleaner rogue security software, under the Computer Spyware Act passed by the Washington State Legislature in 2005. Secure Computer, under consent decree, agreed to pay more than $USD75,000 in restitution to consumers.[16]
In December 2008, the US District Court for Maryland—at the request of the FTC—issued a restraining order against Innovative Marketing Inc, a Kiev-based firm producing and marketing the rogue security software products WinFixer, WinAntivirus, DriveCleaner, ErrorSafe, and XP Antivirus.[17] The company and its US-based web host, ByteHosting Internet Hosting Services LLC, had their assets frozen, were barred from using domain names associated with those products and any further advertisement or false representation.[18]
Law enforcement has also exerted pressure on banks to shut down merchant gateways involved in processing rogue security software purchases. In some cases, the high volume of credit cardchargebacks generated by such purchases has also prompted processors to take action against rogue security software vendors.[19]
Partial list of rogue security software
The following is a partial list of rogue security software, most of which can be grouped into families. These are functionally-identical versions of the same program repackaged as successive new products by the same vendor.[15][20]
|
|
|
References
- ^ abcd'Microsoft Security Intelligence Report volume 6 (July - December 2008)'. Microsoft. 2009-04-08. pp. 92. http://www.microsoft.com/downloads/details.aspx?FamilyID=aa6e0660-dc24-4930-affd-e33572ccb91f&displaylang=en. Retrieved 2009-05-02.
- ^ abDoshi, Nishant (2009-01-19), Misleading Applications – Show Me The Money!, Symantec, https://forums2.symantec.com/t5/blogs/blogprintpage/blog-id/security_risks/article-id/53, retrieved 2009-05-02
- ^Doshi, Nishant (2009-01-21), Misleading Applications – Show Me The Money! (Part 2), Symantec, https://forums2.symantec.com/t5/blogs/blogprintpage/blog-id/security_risks/article-id/54, retrieved 2009-05-02
- ^http://blogs.adobe.com/psirt/2009/12/new_adobe_reader_and_acrobat_v.html
- ^Chu, Kian; Hong, Choon (2009-09-30), Samoa Earthquake News Leads To Rogue AV, F-Secure, http://www.f-secure.com/weblog/archives/00001779.html, retrieved 2010-01-16
- ^Hines, Matthew (2009-10-08), Malware Distributors Mastering News SEO, eWeek, http://securitywatch.eweek.com/seo/malware_distributors_mastering_news_seo.html, retrieved 2010-01-16
- ^Raywood, Dan (2010-01-15), Rogue anti-virus prevalent on links that relate to Haiti earthquake, as donors encouraged to look carefully for genuine sites, SC Magazine, http://www.scmagazineuk.com/rogue-anti-virus-prevalent-on-links-that-relate-to-haiti-earthquake-as-donors-encouraged-to-look-carefully-for-genuine-sites/article/161431/, retrieved 2010-01-16
- ^ ab'Free Security Scan' Could Cost Time and Money, Federal Trade Commission, 2008-12-10, http://www.ftc.gov/bcp/edu/pubs/consumer/alerts/alt121.shtm, retrieved 2009-05-02
- ^CanTalkTech - Fake Green AV disguises as security software with a cause
- ^http://tech.yahoo.com/blog/null/107193
- ^Testimony of Ari Schwartz on 'Spyware', Senate Committee on Commerce, Science, and Transportation, 2005-05-11, http://www.cdt.org/testimony/20050511schwartzspyware.pdf
- ^Leyden, John (2009-04-11). 'Zango goes titsup: End of desktop adware market'. The Register. http://www.theregister.co.uk/2009/04/21/zango. Retrieved 2009-05-05.
- ^Cole, Dave (2006-07-03), Deceptonomics: A Glance at The Misleading Application Business Model, Symantec, https://forums2.symantec.com/t5/blogs/blogprintpage/blog-id/grab_bag/article-id/5, retrieved 2009-05-02
- ^Doshi, Nishant (2009-01-27), Misleading Applications – Show Me The Money! (Part 3), Symantec, https://forums2.symantec.com/t5/blogs/blogprintpage/blog-id/security_risks/article-id/55, retrieved 2009-05-02
- ^ abStewart, Joe (2008-10-22), Rogue Antivirus Dissected - Part 2, SecureWorks, http://www.secureworks.com/research/threats/rogue-antivirus-part-2/?threat=rogue-antivirus-part-2
- ^Attorney General McKenna Announces $1 Million Settlement in Washington’s First Spyware Suit, Washington State Office of the Attorney General, 2006-12-04, http://www.atg.wa.gov/pressrelease.aspx?&id=5926, retrieved 2009-05-02
- ^Ex Parte Temporary Restraining Order RDB08CV3233, United States District Court for the District of Maryland, 2008-12-03, http://www.ftc.gov/os/caselist/0723137/081203innovativemrktgtro.pdf, retrieved 2009-05-02
- ^Lordan, Betsy (2008-12-10), Court Halts Bogus Computer Scans, Federal Trade Commission, http://www.ftc.gov/opa/2008/12/winsoftware.shtm, retrieved 2009-05-02
- ^Krebs, Brian (2009-03-20), 'Rogue Antivirus Distribution Network Dismantled', Washington Post, http://voices.washingtonpost.com/securityfix/2009/03/sunlight_disinfects_rogue_anti.html, retrieved 2009-05-02
- ^Howes, Eric L (2008-11-21), Spyware Warrior - Family Resemblances, http://www.spywarewarrior.com/family_resemblances.htm, retrieved 2009-05-02
- ^Precise Security - Advanced Cleaner
- ^Spyware Warrior - AlfaCleaner
- ^Alpha AntiVirus - Spyware-Review
- ^BleepingComputer - AntiSpyCheck 2.1
- ^BleepingComputer - AntispyStorm
- ^2-Spyare - AntiSpywareExpert
- ^BleepingComputer - Antivirus Soft
- ^2-Spyare - AntiSpywareExpert
- ^2-Spyware - AntiSpywareMaster
- ^Precise Security - AntiSpywareSuite
- ^BleepingComputer - AntiSpyware Shield
- ^BleepingComputer - Antivermins
- ^BleepingComputer - Antivirus 2008
- ^2-Spyware - Antivirus 2009
- ^MyAntispyware - Antivirus XP 2010
- ^Article noting that Antivirus 2010 and Anti-virus-1 are the same
- ^BleepingComputer - Antivirus 2010
- ^BleepingComputer - Antivirus360
- ^BleepingComputer - AntivirusPro2009
- ^Symantec - AntiVirus Gold
- ^PCinDanger - Antivirus Live
- ^BleepingComputer - Antivirus Live
- ^BleepingComputer - Antivirus Master
- ^Symantec - Antivirus XP
- ^SpywareFixPro - Antivirus Pro 2010
- ^411-Spyware - Antivirus System PRO
- ^2-Spyware - Avatod Antispyware
- ^SpywareRemove - Awola
- ^SpywareRemove - BestsellerAntivirus
- ^2-Spyware - Cleanator
- ^McAfee - ContraVirus
- ^SpywareFixPro - Cyber Security
- ^XP-Vista - Doctor Antivirus
- ^2-Spyare - Doctor Antivirus 2008
- ^Symantec Symantec - DriveCleaner
- ^MalwareBytes - EasySpywareCleaner
- ^Symantec - Errorsafe
- ^411-Spyare - GreenAV2009
- ^2-Spyare - IE Antivirus
- ^MalwareBytes - IEDefender
- ^SpywareRemove - InfeStop
- ^Symantec - Internet Antivirus
- ^http://www.precisesecurity.com/rogue/internet-security-2010/
- ^http://www.pcindanger.com/internet-security-2010-removal.html
- ^2-Spyare - KVMSecure
- ^Symantec - MacSweeper
- ^MalwareBytes - MalwareCrush
- ^MalwareBytes - MalwareCore
- ^MalwareBytes - Malware Alarm
- ^2-Spyware - Malware Bell
- ^2-Spyware - Malware Defender
- ^BleepingComputer - MS Antivirus
- ^BleepingComputer MS Antispyware 2009
- ^2-Spyware - MaxAntispy
- ^Dunkelstern Software - Review
- ^Sunbelt Security - Netcom3 Cleaner
- ^411-spyware - PCSecureSystem
- ^BleepingComputer - PC Antispy
- ^ [www.2-spyware.com/remove-pc-antispyware-2010.html]
- ^MalwareBytes - PC Clean Pro
- ^SpywareRemove - PC Privacy Cleaner
- ^MalwareBytes - PerfectCleaner
- ^BleepingComputer - Perfect Defender 2009
- ^BleepingComputer - PersonalAntiSpy Free
- ^BleepingComputer - Personal Antivirus
- ^SpywareWarrior - PAL Spyware Remover
- ^ComputerAssociates - PCPrivacy Tools
- ^SpywareRemove - PC Antispyware
- ^SpywareRemove - PSGuard
- ^BleepingComputer - Rapid AntiVirus
- ^BleepingComputer - Real Antivirus
- ^Precise Security - Registry Great
- ^Bleeping Computer - Safety Alerter 2006
- ^SpywareFixPro - SafetyKeeper
- ^Emsi Soft - SaliarAR
- ^BleepingComputer - Secure Fighter
- ^SpywareRemove - SecurePCCleaner
- ^Bleeping Computer - SecureVeteran
- ^[1]
- ^Spyware-Review Security Tool
- ^Precise Security - Security Toolbar 7.1
- ^PcinDanger - Security Essentials 2010
- ^2-Spyware - Smart Antivirus 2009
- ^SpywareFixPro - Soft Soldier
- ^Symantec
- ^Spyware Warrior - Spy Away
- ^BleepingComputer - SpyCrush
- ^Symantec - SpyDawn
- ^Precise Security - SpyGuarder
- ^BleepingComputer - SpyHeal
- ^411-Spyware - SpyMarshal
- ^Symantec - Spylocked
- ^Symantec - SpySheriff
- ^Symantec - SpySpotter
- ^2-Spyare - SpywareBot
- ^Spyware Warrior - Spyware Cleaner
- ^BleepingComputer - SpywareGuard 2008
- ^Javacool Blog - Fake 'SpywareGuard2008″ rogue – beware
- ^2-Spyware - Spyware Protect 2009
- ^Symantec - Spyware Quake
- ^Spyware Warrior - Spyware Sheriff
- ^Sunbelt Security - Spyware Stormer
- ^MalwareBytes - Spyware Striker Pro
- ^411-Spyware - Spyware Protect 2009
- ^Spyware Warrior - SpywareStrike
- ^Symantec - SpyRid
- ^McAfee - SpyWiper
- ^411-Spyare - System Antivirus 2008
- ^BleepingComputer - System Live Protect
- ^Symantec - SystemDoctor
- ^2-Spyware - System Security
- ^ (aka total security)BleepingComputer - Total Secure 2009
- ^2-Spyware - Trusted Antivirus
- ^Symantec - TheSpyBot
- ^BleepingComputer - UltimateCleaner
- ^Symantec - VirusHeat
- ^Symantec - VirusIsolator
- ^BleepingComputer - VirusLocker
- ^Symantec - VirusProtectPro
- ^Symantec - VirusRemover2008
- ^ComputerAssociates - VirusRemover2009
- ^Symantec - VirusMelt
- ^Sunbelt Security - Virus Ranger
- ^Virus Removal Guru - Virus Response Lab 2009
- ^BleepingComputer - VirusTrigger
- ^BleepingComputer Antivirus Vista 2010
- ^Precise Security - Vista Antivirus 2008
- ^411-Spyware - WinAntiVirus Pro 2006
- ^2-Spyware - WinDefender
- ^SpywareFixPro - Windows Police Pro
- ^BleepingComputer - Windows Protection Suite
- ^Symantec - WinFixer
- ^Symantec - WinHound
- ^Winpc Antivirus
- ^Winpc Defender
- ^Symantec - WinSpywareProtect
- ^BleepingComputer - WinWeb Security 2008
- ^Symantec - WorldAntiSpy
- ^SpywareRemove - XP AntiSpyware 2009
- ^MyAntispyware - XP AntiSpyware 2010
- ^BleepingComputer - XP Antivirus
- ^MyAntispyware - XP Antivirus Pro 2010
- ^[2]
- ^Precise Security - Zinaps AntiSpyware 2008
See also
Super Anti Spyware Free
External links
Free Anti Spyware Programs
- Howes, Eric L (2007-05-04), Spyware Warrior: Rogue/Suspect Anti-Spyware Products & Web Sites, http://www.spywarewarrior.com/rogue_anti-spyware.htm, retrieved 2009-05-02